How to address the growing security risk of IoT devices
The current Internet of Things (IoT) space comes with numerous security vulnerabilities. These vulnerabilities include weak authentication (IoT devices are being used with default credentials), unencrypted messages sent between devices, SQL injections and lack of verification or encryption of software updates. This allows attackers to easily intercept data to collect PII (Personally Identifiable Information), steal user credentials at login, or inject malware into newly updated firmware.
The internet of things, or IoT, is a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.
The definition of the Internet of things has evolved due to the convergence of multiple technologies, real-time analytics, machine learning, commodity sensors, and embedded systems.
Traditional fields of embedded systems, wireless sensor networks, control systems, automation (including home and building automation), and others all contribute to enabling the Internet of things.
In the consumer market, IoT technology is most synonymous with products pertaining to the concept of the “smart home”, covering devices and appliances (such as lighting fixtures, thermostats, home security systems and cameras, and other home appliances) that support one or more common ecosystems, and can be controlled via devices associated with that ecosystem, such as smartphones and smart speakers.
Security is the biggest concern in adopting Internet of things technology. In particular, as the Internet of things spreads widely, cyber attacks are likely to become an increasingly physical (rather than simply virtual) threat.
The IoT concept has faced prominent criticism, especially in regards to privacy and security concerns related to these devices and their intention of pervasive presence.
Concerns have been raised that the IoT is being developed rapidly without appropriate consideration of the profound security challenges involved and the regulatory changes that might be necessary.
Most of the technical security concerns are similar to those of conventional servers, workstations and smartphones, but security challenges unique to the IoT continue to develop, including industrial security controls, hybrid systems, IoT-specific business processes, and end nodes.
In a January 2014 article in Forbes, a cyber-security columnist listed many Internet-connected appliances that can already “spy on people in their own homes” including televisions, kitchen appliances, cameras, and thermostats.
Computer-controlled devices in automobiles such as brakes, engine, locks, hood and trunk releases, horn, heat, and dashboard have been shown to be vulnerable to attackers who have access to the on-board network.
In some cases, vehicle computer systems are Internet-connected, allowing them to be exploited remotely. For example, a hacker can gain unauthorized access to IoT devices due to their set-up; because these devices are connected, Internet-enabled, and lack the necessary protective measures.
By 2008 security researchers had shown the ability to remotely control pacemakers without authority. Later hackers demonstrated remote control of insulin pumps and implantable cardioverter defibrillators.
Many IoT devices have severe operational limitations on their physical size and by extension the computational power available to them. These constraints often make them unable to directly use basic security measures such as implementing firewalls or using strong cryptosystems to encrypt their communications with other devices.
The U.S. National Intelligence Council in an unclassified report maintains that it would be hard to deny “access to networks of sensors and remotely-controlled objects by enemies of the United States, criminals, and mischief makers…
An open market for aggregated sensor data could serve the interests of commerce and security no less than it helps criminals and spies identify vulnerable targets. Thus, massively parallel sensor fusion may undermine social cohesion, if it proves to be fundamentally incompatible with Fourth-Amendment guarantees against unreasonable search.
In general, the intelligence community views the Internet of things as a rich source of data.
"Despite high-profile and alarming hacks, device manufacturers remain undeterred, focusing on profitability over security. Consumers need to have ultimate control over collected data, including the option to delete it if they choose...Without privacy assurances, wide-scale consumer adoption simply won't happen."
There have been a range of responses to concerns over security. The Internet of Things Security Foundation (IoTSF) was launched on 23 September 2015 with a mission to secure the Internet of things by promoting knowledge and best practice. Its founding board is made from technology providers and telecommunications companies. In addition, large IT companies are continuously developing innovative solutions to ensure the security for IoT devices. In 2017, Mozilla launched Project Things, which allows to routing IoT devices through a safe Web of Things gateway.
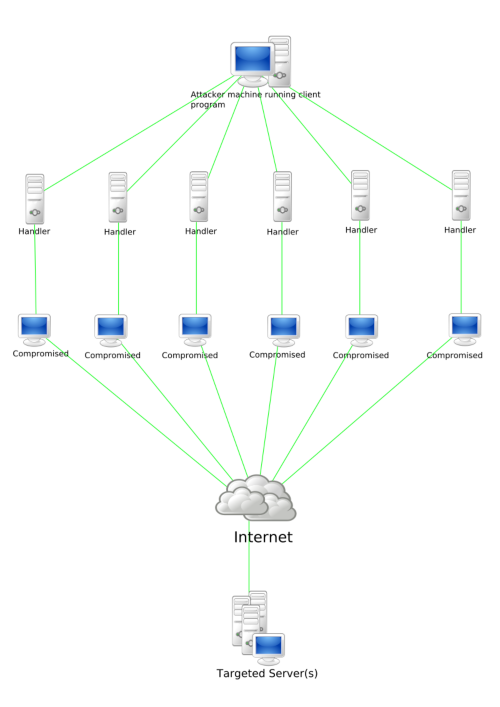
Botnets: a growing threat to the Internet of things
A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform distributed denial-of-service attack (DDoS attack), steal data, send spam, and allows the attacker to access the device and its connection.
Botnets are always advancing, botnets are a prevalent security risk because they are constantly changing and being improved while many deployed IoT devices remain vulnerable. Over the past few years, many forms of botnets have been created, taking advantage of the evolution of the technology industry and advances in software engineering.
To tackle botnets, Hughes says all networks and all devices need not only high levels of security monitoring and regular updates, but also known levels of trust within a system. “These levels of trust are starting to be built upwards from the chip manufacturers as well as the device and software industry,” he says. “Of course, it only takes one release of a product at any level cutting some corners to get to market, to leave something wide open for hackers.”
It may be that attackers are often one step ahead, but by being more proactive, security teams can help to mitigate the potentially damaging effects of IoT connected devices.
Five Basic Ways to Help Mitigate Botnets Attacks on IoT Devices
- Ensure factory default passwords are replaced with strong ones
- Keep systems up to date and patched: Bots, like other malware, often exploit unpatched vulnerabilities in order to propagate and compromise vulnerable systems. Patched systems provide less opportunity for infection.
- Block unsolicited inbound traffic at your perimeter firewall: Even if computer systems inside the network are compromised, they can’t be activated if the attacker can’t communicate with them.
- Run antivirus software: Known bot threats can be detected and removed by antivirus software products. Performing periodic scans with up-to-date antivirus software can locate and remove bot infections.
- Use intrusion detection or intrusion prevention system monitoring: An intrusion detection or intrusion prevention system running on the internal network can identify suspicious activity and alert you or take action to halt it.
Learn more

