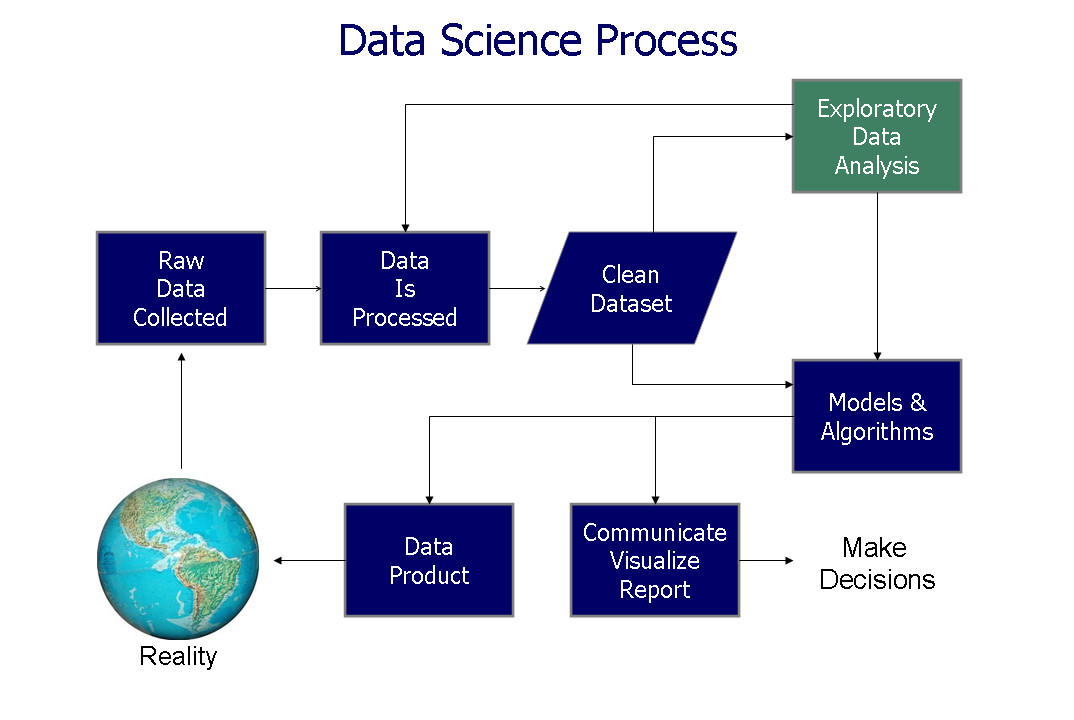
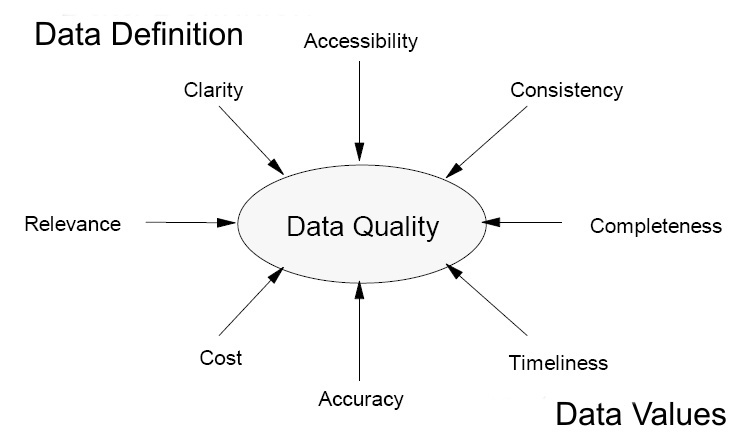
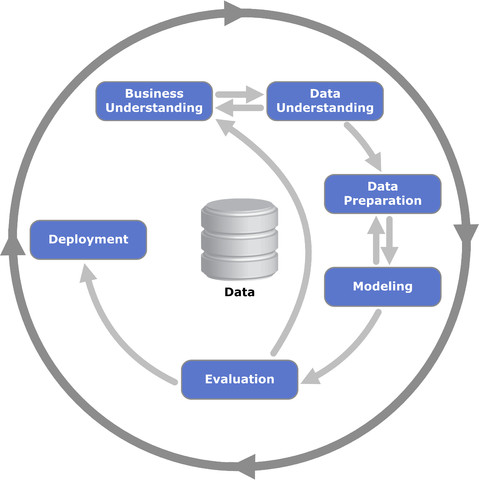
It’s difficult to imagine the power that you’re going to have when so many different sorts of data are available.
How to use Artificial Intelligence in Marketing
You can Use the power of artificial intelligence and machine learning to elevate the abilities of your marketing team to a higher level, and start create an impact that promotes engagement and meaningful customer relationships.