Why You Need To Ensure Data Integrity Before You Lose it
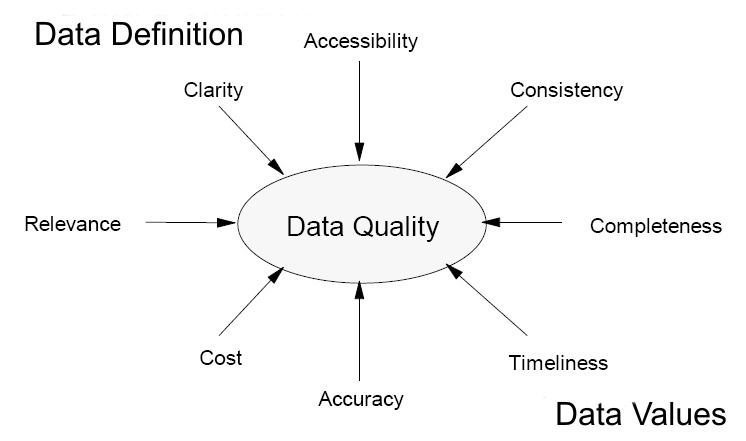
Detecting and Responding to Ransomware and Other Destructive Events No organization is immune from cybersecurity threats and attacks, which can range from minor inconveniences to major catastrophic events that may take months sometimes years to overcome. Events such as ransomware, destructive malware, insider threats, and even honest mistakes, can threaten an organization’s infrastructure, not to mention its most valuable asset—its reputation. Moreover, database records and structures, system files, configurations, user files, application code, and customer data are all at risk should an event occur.